25 TCP - Simple Mail Transfer Protocol (SMTP)
Enumerate Server Capabilities
A servers capabilities (encryption, authentication, etc.) are sent in response to the EHLOcommand. The HELOcommand, on the other hand, is silent.
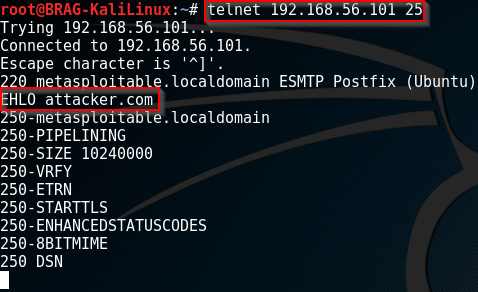
Step 1 - Connect to SMTP service via Telnet
telnet <target_server> <port>
Step 2 - Issue EHLOCommand
EHLO <some_system_name>
Enumerate STARTTLS Encryption Configuration
When the keyword STARTTLS appears in the EHLOoutput, the server supports encryption.
You can not test this via Telnet, however, since the server accepts only encrypted data after entering this command and acknowledges any plaintext commands with an interruption of the connection.
To test the encrypted communication you can use openssl instead.
openssl s_client -connect <servername>:25 -starttls -smtp
Enumerate SMTP Users
SMTP can help the penetration tester to perform username enumeration via the EXPNand VRFYcommands if these commands have not been disabled by the system administrator. The role of the EXPNcommand is to reveal the actual address of users aliases and lists of email and VRFYwhich can confirm the existance of names of valid users.
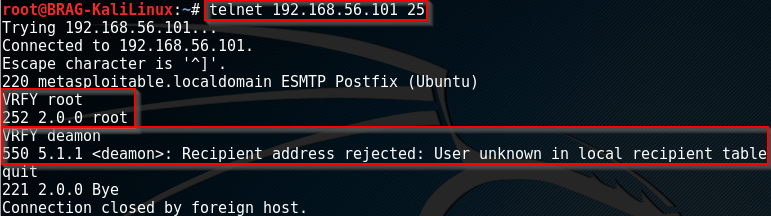
Enumeration with VRFY command
Step 1 - Connect to SMTP service via Telnet
telnet <target_server> <port>
Set 2 - Enumerate Users with VRFY command
VRFY <username>
COUNTERMEASURE
Disable the VRFY command for the Mail Relay server.
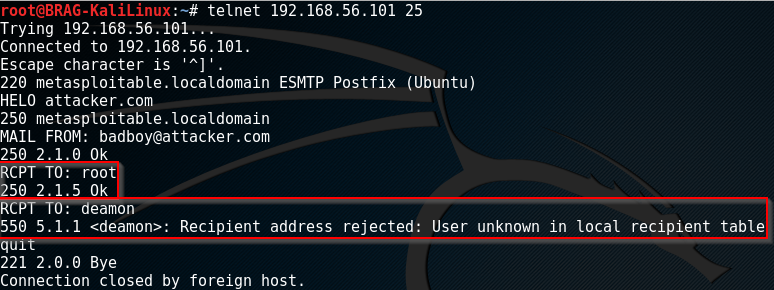
Enumeration with RCPT TO: command
Step 1 - Connect to SMTP service via Telnet
telnet <target_server> <port>
HELO <some__system_name>
MAIL FROM: <some_sender_address>
--> Note: You could also start your user enumeration with the MAIL FROM: command, but just for the first username.
Set 2 - Enumerate Users with RCPT TO: command
RCPT TO: <username>
COUNTERMEASURE
As the RCPT TO: command is necessary for email creation, sending and handling it cannot be disabled. This enumeration technique should always work.
Enumeration with EXPNcommand
The EXPNcommand allows you to expand a mailing list or alias, to see where mail addressed to the alias actually goes. For example, many organizations alias postmaster to root, so that mail addressed to postmaster will get delivered to the system administrator. Issuing EXPN postmaster via SMTP would reveal that postmaster is aliased to root.
The EXPNcommand can be used by attackers to learn about valid usernames on the target system. On some SMTP servers, EXPNcan be used to show the subscribers of a mailing list -- subscription lists are generally considered to be sensitive information.
COUNTERMEASURES
Disable the EXPNcommand as it is only useful when debugging mailing lists, but it should be disabled on production servers.
SMTP Enumeration Tools
For the use of tools it is helpful to have a good list of usernames to test. While standard username lists (mostly build into such tools) can be a good start, the Reconnaissance phase should also yield some more usernames / email addresses to run these tests against.
Nmap with NSE Script "smtp-enum-users.nse"
nmap –script smtp-enum-users.nse <target_system>
Metasploit Auxilary Scanner "smtp_enum"
auxiliary/scanner/smtp/smtp_enum
Standalone Perl Script "smtp-user-enum"
perl smtp-user-enum.pl -M VRFY -U <userlist> -t <target_system>